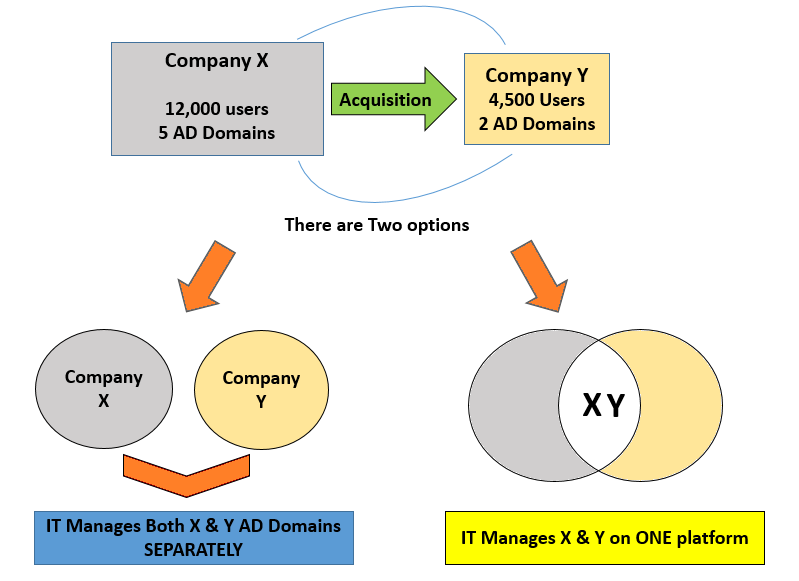
Are you in the midst of a merger, acquisition, or is your organization complex? If so you may be experiencing this challenge.
The Merger, Acquisition, & Complex Organization Problem
Sep 14, 2016 / by Bird Rock Blogger posted in IT, Security, technology solutions, access managment, Active Directory, migration, user efficiency, acquisition, merger, single sign on
Three Reasons Why I.T. is Important to Your Organization
Sep 14, 2016 / by Bird Rock Blogger posted in IT, IT Solutions, Security, technology solutions, Bird Rock Systems
The digital age has brought amazing innovations to the working world like Skype, Dropbox, Office 365, and so much more. At the same time, the digital age has brought many headaches and concerns. Some in the form of a disastrous Ransomware attack on healthcare systems and others of less grave consequences such as a faulty Wi-Fi connection.
Palo Alto Firewall: PAN-OS 7.0 is here!
Jul 10, 2015 / by Joseph Javien posted in Palo Alto Networks, PAN, PAN-OS 7.0, Security
Written By Larry Hoehn
Here’s a brief overview of a couple of the new features and upgrades included with the new release PAN-OS 7.0. At a high level, the new version addresses these issues:
- Turning alerts into action. According to a report from Ernst & Young, 33% of security professionals don’t know how long it takes to respond to alerts.
- Discovering unknown threats. According to the 2014 Verizon DBIR, there were $400M financial losses from 700 million compromised records. Much was from unknown threats and 75% of attacks spread from Victim 0 to Victim 1 within 24 hours.
To help with the first challenge, the ACC tab has been redesigned with actionable data:
That new widget shows application usage – the bigger the box, the more application usage on the network. Red means critical, orange means important. You can quickly get more detail to find critical information with a few clicks. For example, application and user activity:
And network activity with threat levels:
To help with the second challenge (discovering unknown threats): Since WildFire already analyzes 20 million samples per week (and growing), Palo Alto added multi-version detailed analysis with a single virtual machine for different versions of software. For example, a file can be run through several versions of Acrobat to see if malware is targeted to a specific version of that application. They’ve also added a new verdict to WildFire to quickly analyze threats. Previously just “malware” or “benign”, a new verdict includes “Grayware”, for things like Adware and Trackware.
A new feature is the automated correlation engine. It’s an analytics tool that verifies compromised hosts in your network. It scrutinizes isolated events across multiple logs on the firewall, examines patterns, and correlates events to identify actionable information such as host-based activities that indicate a compromised host. The engine includes correlation objects that are defined by the Palo Alto Networks Malware Research team. These objects identify a suspicious sequence of events that indicate a malicious outcome. Correlation objects trigger alerts when they match on patterns that indicate a compromised host on your network. For example:
In the example above, if these four indicators are present, we have an automated trigger to alert there is a compromised host. The following screenshot illustrates how the automated correlation engine combines indicators of threats and highlights the resulting situation as “critical”, which means it exhibits signs of worm activity to help you determine where to focus effort for fast remediation.
There are many more updated capabilities, but these were a few I though you would think are interesting. When you get a chance, take a look at the new version and let me know your thoughts!
BYOD – It can be done safely - Part 3
Nov 06, 2014 / by Joseph Javien posted in Firewall, Security, BYOD
Written By Larry Hoehn
In my previous post, I discussed how wireless technology has a role when providing secure BYOD access. Along those lines, this article explains firewall technology’s role for a secure BYOD initiative.
Today's corporate workforce expects to access their corporate networks from personal mobile devices used both inside and outside the corporate walls. Providing this access to employees and contractors drives productivity gains and fosters innovation. While the benefits can justify the requirement, BYOD introduces elements of risk that legacy technologies have a difficult time addressing.
Old-school firewall port and protocol-based security focus on attacks directed from the outside in. This method assumes that devices inside the network are trusted, since they allow access without consideration for the user’s identity, the device type, or the application in use. This leaves organizations open to attacks from inside the network.
Modern solutions take a new approach – these solutions map user and device information to network security policies, enabling IT to enforce what a user can access with a particular device and authorized application. Firewall policies can also enforce, among other things, bandwidth on a per-user or per-department basis.
How this works:
- Users and devices connect to the network.
- Wired or Wireless architecture shares contextual data (IP address, device type, user role) with the firewall.
- The firewall monitors for policy violations to the network based on who and what is connected to the infrastructure.
- Applications can be controlled based on who and what is connected to the infrastructure, or blocked if there’s no legitimate use.
The big benefit:
Security against known and unknown malware, zero-day exploits, and advanced persistent threats. The firewall automatically implements and enforces protection in near real-time to defend against dynamic attacks.
Stay tuned for my next article, where I’ll discuss a solution with a product use case!
BYOD – It can be done safely - Part 2
Aug 20, 2014 / by Joseph Javien posted in Security, Wireless, BYOD
Written By: Larry Hoehn
In my last post, I discussed combining technologies to provide secure BYOD access. Before we jump into the specifics, let’s pick apart the technology components – starting with the wireless technology.
Modern wireless solutions provide awareness of all traffic across the network to support a variety of users, devices, and applications. Old-school network architectures mandate that parallel networks be constructed to address different needs– for example, one VLAN for employees, a second for full-time contractors, and a third for guests. In other cases, multiple SSIDs were required. Today’s design methods support multiple user categories on a single network.
How It Works
During the network sign-on process, the identity and role of each user or device is learned. Employees and other authorized users may be treated as a single class, or divided according to a series of administrator-defined policies. These policies follow the user throughout the network, and are applied uniformly across wireless, wired, and remote access connections.
Learn This
This entire premise is made possible by using a firewall instance around every user: tightly controlling what the user is permitted to do and providing separation between user classes. To provide the highest level of security, the solution requires knowledge of user identity when making access control decisions. Our wireless and next-generation firewall solutions enable us to deliver this level of security.
The wireless technologies we work with provide us an important point of authentication and policy enforcement. Policy control is tied to user identity rather than port, IP address, or MAC address. This makes it impossible for a user to bypass security controls, except in the case of breached credentials. (Protect your passwords! We will talk about that in a future post.)
A use case for this is a guest user on the guest network that attempts to bypass the guest network by configuring a laptop with the MAC address and IP address of an employee also known as spoofing an address. With the proper policies in place, that malicious guest user will be denied access to the employee network because of his guest privileges regardless of mac address or IP address of the device.
Role Based Policy, Granular Control & API Integration
Taking this a step further, role-based policies can limit maximum and guarantee minimum amounts of bandwidth for a particular user or class of users. This allows IT to provision a specified amount of service to bandwidth-hungry applications. In addition, granular control of users, such as automatic disconnect from the network, role re-assignment, and dynamic updates of firewall policies are available as well.
Behind the scenes, additional functionality is enabled by powerful API integration between various IT solutions from different manufacturers. The APIs can enable captive portal authentication systems, or query external databases to control advanced behavior. This includes integration with solutions that provide services such as virus protection, content inspection and filtering, intrusion detection and prevention, and content transformation.
An example of this could be a posture assessment. A check can be performed to make sure anti-virus scans have been run within the past week and provide different network access depending on the criteria of this test.
We Can Help!
As you can see, there is a lot of flexibility, control and added security that can be delivered with the proper solutions, policy and controls in place when it comes to BYOD. For more information, please contact your local Bird Rock Systems Account Manager or send us a message on our Contact page.
In my next post, I will do a deeper dive on the next-generation firewall part of the equation. Then I’ll wrap the wireless and firewall technologies together. Stay tuned!
Photo credit: John.Karakatsanis / Foter / Creative Commons Attribution-ShareAlike 2.0 Generic (CC BY-SA 2.0)
BYOD – It can be done safely
Jun 30, 2014 / by Larry Hoehn posted in Security
There is no silver bullet for the ‘Bring Your Own Device’ concept, but by embracing BYOD, employees can be more productive and your company can reduce capital expenses. Safely allowing devices to connect to your network is about policy and layers of technology, many of which you probably already have in place today if you allow employees to connect via VPN to your network from their home PC. Allowing devices without those considerations can be reckless to your company and its employees.
I’ll discuss a number of aspects to consider for BYOD in a series of posts. This post focuses on a high-level example of technology that can help securely permit employee devices to access corporate resources.
Combining next generation wireless solutions and next generation firewalls provide security for guest and employee owned mobile devices on enterprise networks. You can securely enable Bring Your Own Device and Guest Access while maintaining compliance. These technologies can share user, device and application information to monitor and enforce application usage policies on smartphones, tablets and laptops – regardless if the devices is connected via Wi-Fi, wired network, a cellular provider, or a VPN connection.
Traditional firewall policies are based on IP address, but the allocation of IP addresses to corporate and guest users means that the user and group associations are not reflected in those policies. Imagine your firewall is seamlessly integrated with enterprise directories to identify users of the corporate network. Now imagine your BYOD management solution utilized that same technology to guest users and employee owned mobile devices.
Security policies on the next-generation firewall can be defined based on the user and/or group membership. This cohesive system provides complete visibility and control over the applications and resources available to all network users. The combined solution provides safe enablement of resources in situations such as:
- Securing users and devices on guest Wi-Fi networks
- Allowing access to applications while protecting from potentially dangerous content
- Full visibility (traffic by user and application) and control of network resources
- Integrated wired and wireless policies compliance and enforcement
Stay tuned for more posts on this topic.
San Diego Daily Transcript: How secure is your IT infrastructure?
Mar 10, 2014 / by Joseph Javien posted in In The News, IT Solutions, Security, Bird Rock Systems
When it comes to your company’s technology infrastructure you want to build it with top of the line, secure solutions. Bird Rock Systems is a local technology solutions provider founded in 2003 that does just that!
UT San Diego: Use of Personal Devices at Work Gaining Acceptance More Personal Devices Seen at Work
Nov 25, 2013 / by Joseph Javien posted in In The News, Jim Matteo, Security, BYOD
Growing BYOD trend still raises security concerns
These days, employees are bringing to their workplaces their own personal devices, like smart phones, tablets and laptops.
In the past, a lot of companies weren’t too keen on the idea of allowing workers to use their own equipment. The overriding concern was about security of company data, as well as being uncomfortable with employees storing work information on personal devices.
Now, it appears that such thinking is starting to change. There’s a phenomenon spreading through business across the country that’s known as Bring Your Own Device, or BYOD.
“As companies keep recruiting millennials, BYOD is going to be important in keeping them happy,” said Jim Matteo, CEO of San Diego-based Bird Rock Systems, which provides network security solutions for a wide variety of businesses.
For the full story visit:
http://www.utsandiego.com/news/2013/nov/25/tp-use-of-personal-devices-at-work-gaining/
Get a Panoramic View of your firewalls with Panorama
Sep 18, 2012 / by Larry Hoehn posted in Security
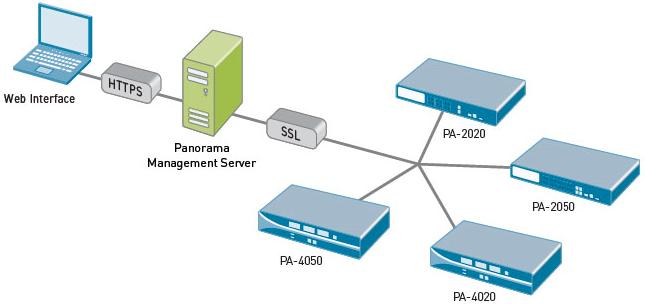
Panorama is a virtual appliance available from Palo Alto Networks that provides visibility and controller over multiple PAN next generation firewalls. All logs and content data get bubbled up into an aggregate view. Reports are based on that aggregate view – all activity from all firewalls on one report. This feature is licensed separately from the firewalls themselves.
This is a high-level overview of the architecture:
The Panorama GUI looks almost exactly like the traditional PAN GUI, which means a very small learning curve to get started with centralized visibility and control of your PAN environment.
You get 3 benefits:
- Centralized device and policy management of multiple Palo Alto Network firewalls
- View applications, users and content flowing across multiple Palo Alto Network firewalls
- Complete device management in a secure manner from a central location -- CLI or GUI are both included
With Panorama and a network of Palo Alto Networks firewalls in place, you can deploy global or local policies to block bad applications, protect the business applications and promote the secure use of end-user applications.
Panorama is a VMware image, purchased separately from the firewall itself, downloadable from the Palo Alto Networks support site. To install:
- Register the Panorama serial number on the support site.
- Download Panorama image zip file from the download page. Unzip the file.
- Open vCenter or your vSphere management interface of choice, and deploy the Panorama OVF on a thick provisioned disk.
- Use a 4GB maximum RAM limit if you have 10 or more managed firewalls.
- Use a quad core CPU for the best performance, especially with high logging rates.
- Use RAID 1/0 for the logging virtual disk for better write performance. The drives can be optimized for sequential writing of a small number of large files.
- Network based storage introduces latency and should be avoided when there are high logging rates.
- Start the virtual machine and login to the virtual machine’s console using the default login credentials.
- Configure the networks settings at the CLI and commit the changes.
- Login to the GUI with your browser using the default login credentials.
- Change the admin login/password.
- Assign the serial number, configure time/NTP, and import or generate a SSL certificate.
- Add the firewall’s serial numbers for the devices to manage.
- Commit the changes and you’re good to go.
Once you can see the devices, you can define a set of devices that are treated as a unit when applying policies: Panorama > Device Groups. From there, you can see which device configurations are out of sync. With caution, you can “commit all” next to each device in Panorama. I say ‘with caution’ because interesting things can happen with security policies and other configuration tidbits that are slightly askew (e.g. upper case vs. lower case, etc.).
Panachrome: More GUI functionality for Palo Alto Networks Firewalls
Sep 04, 2012 / by Larry Hoehn posted in Security
I ran into a free extension for the Google Chrome browser in early 2012 and I use the extension often enough that I forgot it was an extension until a customer asked about it during a firewall demonstration. If you have a Palo Alto firewall running 4.1, check this out. Thanks to ‘lmori’ for posting this on the Palo Alto Networks DevCenter (support login required).
The extension allows the GUI to display a bit of information normally only available from CLI. The extension uses an API introduced in PAN-OS 4.1. Installation steps are at the bottom of this post. This works with Chrome browsers only.
You need to be logged on the firewall with superuser privileges to use the extension. The PAN logo will appear on the Chrome URL bar:
Here are some of the coolness you’ll notice. Desktop notifications on jobs completion:
DP Resource monitor - the output of "show running resource-monitor" command:
Session info - the output of "show session info" command:
Counters global - the output of "show counters global" command:
Interface traffic rate - the average rates of physical and logical interfaces:
INSTALLATION
- Login to the Palo Alto Networks support site.
- Go to lmori’s post: https://live.paloaltonetworks.com/docs/DOC-1986
- Follow the link to grap the crx file.
- Drag and drop the .crx file on a Chrome window. Your mileage will vary with this step, depending on the Chrome version you’re using. You may need to play with the Chrome options that the browser to install an extension that is outside of the Chrome Web Store.
- That’s it. Use Chrome to login to your firewall and enjoy!