Information Technology and the team behind it is more crucial to business than ever before. The old way of doing things has almost completely disappeared and everything is going digital. There are more apps, more mobile users, basically more of everything related to technology and data.
Why Do We Battle Our IT?
Mar 12, 2017 / by Bird Rock Blogger posted in IT Solutions, information technology, IT Services, Cyber Security, Optimization
Ransomware: To Pay or Not to Pay?
Oct 17, 2016 / by Bird Rock Blogger posted in IT, IT Solutions, Security, Innovation, ransomware, information technology, zero day threats
You know your business better than anyone else. How much money will you lose due to system downtime? What is your cost to recovery? How much is your data worth? I think the answer here is simple; pay the ransom if it is going to seriously affect your business.
Advanced Endpoint Protection: A different approach
Jul 29, 2016 / by Joseph Javien posted in information technology, strategy
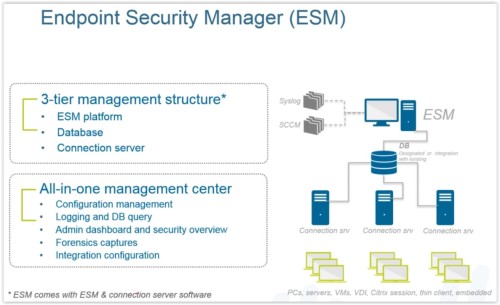
When most people think of endpoint protection, they think of antivirus software. But targeted attacks can use a new threat that is able to evade detection or some embedded malicious content in an iFrame could bypass antivirus software leading to even more dangerous threats that most are unprotected from.
Palo Alto Networks acquired Cyvera and branded this product as ‘Traps’. You may have seen similar products on the market, like Microsoft EMET. However, Traps integrates into WildFire, Palo Alto Network’s sandboxing technology. Plus it’s a mature product, as you’ll see below.
Traditional antivirus-based protection is based on signatures – it requires prior knowledge of the threat in order to be effective. According to Palo Alto Networks, over 20,000 new forms of malware are created per day. Antivirus-based solutions have to build signatures against all of those new forms, then distribute those signatures out to all the endpoints. This takes time and has a negative impact on the effectiveness of many antivirus solutions.
Traps is very effective against zero-day based attacks. The attacker would run into one of the exploit prevention modules within Traps, the process gets terminated, the user is alerted that an attack was prevented, and the administrator receives an alert. Traps collects forensics and provide it to the administrator.
To learn more about Cyber Security threats and prevention check out our blog where you can find dozens of articles written by our expert team members.