The cloud is becoming increasingly integral to businesses worldwide, particularly as many employees continue to work from home. SASE (Secure Access Service Edge) helps keep users protected, whether they are working on-site, from home, or on the go while simultaneously simplifying the protection process.
Larry Hoehn
Recent Posts
The Businesses Guide to Ransomware
Jul 28, 2020 / by Larry Hoehn posted in ransomware, Business, Cybersecurity, Small Business
BYOD – It can be done safely
Jun 30, 2014 / by Larry Hoehn posted in Security
There is no silver bullet for the ‘Bring Your Own Device’ concept, but by embracing BYOD, employees can be more productive and your company can reduce capital expenses. Safely allowing devices to connect to your network is about policy and layers of technology, many of which you probably already have in place today if you allow employees to connect via VPN to your network from their home PC. Allowing devices without those considerations can be reckless to your company and its employees.
I’ll discuss a number of aspects to consider for BYOD in a series of posts. This post focuses on a high-level example of technology that can help securely permit employee devices to access corporate resources.
Combining next generation wireless solutions and next generation firewalls provide security for guest and employee owned mobile devices on enterprise networks. You can securely enable Bring Your Own Device and Guest Access while maintaining compliance. These technologies can share user, device and application information to monitor and enforce application usage policies on smartphones, tablets and laptops – regardless if the devices is connected via Wi-Fi, wired network, a cellular provider, or a VPN connection.
Traditional firewall policies are based on IP address, but the allocation of IP addresses to corporate and guest users means that the user and group associations are not reflected in those policies. Imagine your firewall is seamlessly integrated with enterprise directories to identify users of the corporate network. Now imagine your BYOD management solution utilized that same technology to guest users and employee owned mobile devices.
Security policies on the next-generation firewall can be defined based on the user and/or group membership. This cohesive system provides complete visibility and control over the applications and resources available to all network users. The combined solution provides safe enablement of resources in situations such as:
- Securing users and devices on guest Wi-Fi networks
- Allowing access to applications while protecting from potentially dangerous content
- Full visibility (traffic by user and application) and control of network resources
- Integrated wired and wireless policies compliance and enforcement
Stay tuned for more posts on this topic.
Get a Panoramic View of your firewalls with Panorama
Sep 18, 2012 / by Larry Hoehn posted in Security
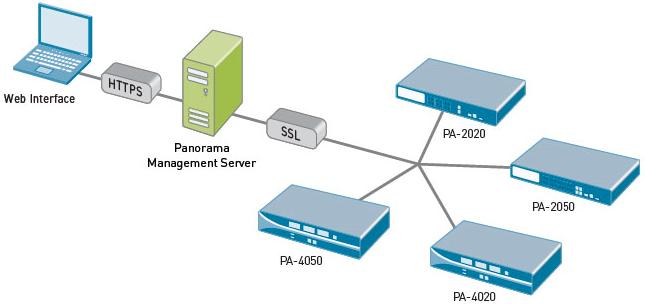
Panorama is a virtual appliance available from Palo Alto Networks that provides visibility and controller over multiple PAN next generation firewalls. All logs and content data get bubbled up into an aggregate view. Reports are based on that aggregate view – all activity from all firewalls on one report. This feature is licensed separately from the firewalls themselves.
This is a high-level overview of the architecture:
The Panorama GUI looks almost exactly like the traditional PAN GUI, which means a very small learning curve to get started with centralized visibility and control of your PAN environment.
You get 3 benefits:
- Centralized device and policy management of multiple Palo Alto Network firewalls
- View applications, users and content flowing across multiple Palo Alto Network firewalls
- Complete device management in a secure manner from a central location -- CLI or GUI are both included
With Panorama and a network of Palo Alto Networks firewalls in place, you can deploy global or local policies to block bad applications, protect the business applications and promote the secure use of end-user applications.
Panorama is a VMware image, purchased separately from the firewall itself, downloadable from the Palo Alto Networks support site. To install:
- Register the Panorama serial number on the support site.
- Download Panorama image zip file from the download page. Unzip the file.
- Open vCenter or your vSphere management interface of choice, and deploy the Panorama OVF on a thick provisioned disk.
- Use a 4GB maximum RAM limit if you have 10 or more managed firewalls.
- Use a quad core CPU for the best performance, especially with high logging rates.
- Use RAID 1/0 for the logging virtual disk for better write performance. The drives can be optimized for sequential writing of a small number of large files.
- Network based storage introduces latency and should be avoided when there are high logging rates.
- Start the virtual machine and login to the virtual machine’s console using the default login credentials.
- Configure the networks settings at the CLI and commit the changes.
- Login to the GUI with your browser using the default login credentials.
- Change the admin login/password.
- Assign the serial number, configure time/NTP, and import or generate a SSL certificate.
- Add the firewall’s serial numbers for the devices to manage.
- Commit the changes and you’re good to go.
Once you can see the devices, you can define a set of devices that are treated as a unit when applying policies: Panorama > Device Groups. From there, you can see which device configurations are out of sync. With caution, you can “commit all” next to each device in Panorama. I say ‘with caution’ because interesting things can happen with security policies and other configuration tidbits that are slightly askew (e.g. upper case vs. lower case, etc.).
Panachrome: More GUI functionality for Palo Alto Networks Firewalls
Sep 04, 2012 / by Larry Hoehn posted in Security
I ran into a free extension for the Google Chrome browser in early 2012 and I use the extension often enough that I forgot it was an extension until a customer asked about it during a firewall demonstration. If you have a Palo Alto firewall running 4.1, check this out. Thanks to ‘lmori’ for posting this on the Palo Alto Networks DevCenter (support login required).
The extension allows the GUI to display a bit of information normally only available from CLI. The extension uses an API introduced in PAN-OS 4.1. Installation steps are at the bottom of this post. This works with Chrome browsers only.
You need to be logged on the firewall with superuser privileges to use the extension. The PAN logo will appear on the Chrome URL bar:
Here are some of the coolness you’ll notice. Desktop notifications on jobs completion:
DP Resource monitor - the output of "show running resource-monitor" command:
Session info - the output of "show session info" command:
Counters global - the output of "show counters global" command:
Interface traffic rate - the average rates of physical and logical interfaces:
INSTALLATION
- Login to the Palo Alto Networks support site.
- Go to lmori’s post: https://live.paloaltonetworks.com/docs/DOC-1986
- Follow the link to grap the crx file.
- Drag and drop the .crx file on a Chrome window. Your mileage will vary with this step, depending on the Chrome version you’re using. You may need to play with the Chrome options that the browser to install an extension that is outside of the Chrome Web Store.
- That’s it. Use Chrome to login to your firewall and enjoy!
Palo Alto Firewalls are HOT, thanks to WildFire
Aug 22, 2012 / by Larry Hoehn posted in Security
As you may know by now, Palo Alto Networks is a relatively new network security company. Its next-generation firewalls (NGF) provide granular visibility and control of applications and content. In addition to traditional firewall criteria, these firewalls can identify applications regardless of port, protocol, evasive tactic or SSL encryption. This is a lot of functionality packed into one box.
In November 2011, Palo Alto Networks extended network security to combat targeted malware with a WildFire cloud-based engine. WildFire submits EXE and DLL files to their cloud-based, virtualized environment for automatic analysis of malicious activity. It runs the files in a vulnerable environment and watches for malicious behaviors and techniques, such as modifying system files, disabling security features, or using a variety of methods to evade detection.
What’s so great about this, you may ask? Malware is distributed by a wide variety of web applications, in addition to the traditional HTTP web-browsing and email. The ability to detect, remediate and investigate unknown malware has become a practical part of a threat prevention strategy, like IPS and URL filtering.
Scenario #1: You’re inspecting email attachments for malware but do not have the ability to scan other applications. Applications that tunnel within HTTP or other protocols can carry malware that will be invisible to a traditional anti-malware solution.
Scenario #2: You have a firewall with integrated cloud-based malware analysis. This will expand your view to other applications, pull the traffic apart and go a level deeper, and addresses the challenge of modern malware.
How does it work? Unknown and potentially-malicious files are executed in a cloud-based sandbox. If the files are confirmed to be malicious, it automatically generates new signatures for both the file and for any traffic generated by the malicious file. These signatures are distributed with regular signature updates. Plus, you get an actionable analysis of exactly how the malware behaves – who was targeted and what application delivered the threat.
That sounds great, but how do I use it? At this time, WildFire is a free feature included with PAN-OS 4.1 or newer. If you already own a Palo Alto Networks firewall, enable it!
- Login to your firewall and go to Device > Setup > WildFire
- Go with the defaults settings, or make changes based on your requirements.
- Configure file blocking profiles (PE file type) to include the “forward” or “continue-and-forward” action.
- Incorporate file blocking profiles in security policies, just like other file blocking profiles.
That’s all you need to do on the firewall. Now login to the WildFire portal:
- Go to https://wildfire.paloaltonetworks.com, and login with your support credentials.
- Optional: Change your time zone and/or email notification settings.
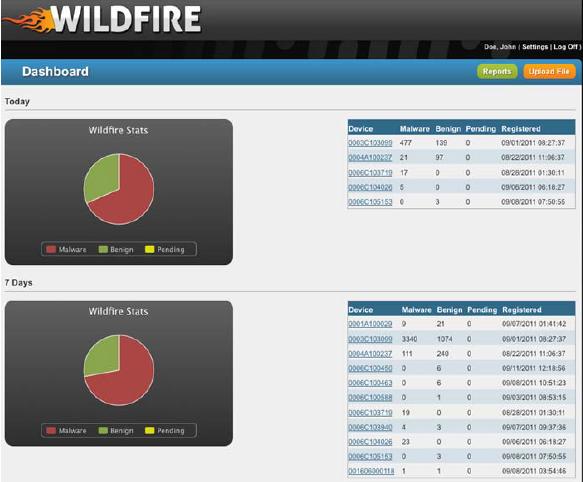
- The initial screen is the dashboard, similar to the following:
- Click the ‘Reports’ button to see details of the potential and actual threats that have been processed in the cloud:
Do you have any interesting stories about WildFire, or thoughts about this article? Please chime in with a comment.