As you may know by now, Palo Alto Networks is a relatively new network security company. Its next-generation firewalls (NGF) provide granular visibility and control of applications and content. In addition to traditional firewall criteria, these firewalls can identify applications regardless of port, protocol, evasive tactic or SSL encryption. This is a lot of functionality packed into one box.
In November 2011, Palo Alto Networks extended network security to combat targeted malware with a WildFire cloud-based engine. WildFire submits EXE and DLL files to their cloud-based, virtualized environment for automatic analysis of malicious activity. It runs the files in a vulnerable environment and watches for malicious behaviors and techniques, such as modifying system files, disabling security features, or using a variety of methods to evade detection.
What’s so great about this, you may ask? Malware is distributed by a wide variety of web applications, in addition to the traditional HTTP web-browsing and email. The ability to detect, remediate and investigate unknown malware has become a practical part of a threat prevention strategy, like IPS and URL filtering.
Scenario #1: You’re inspecting email attachments for malware but do not have the ability to scan other applications. Applications that tunnel within HTTP or other protocols can carry malware that will be invisible to a traditional anti-malware solution.
Scenario #2: You have a firewall with integrated cloud-based malware analysis. This will expand your view to other applications, pull the traffic apart and go a level deeper, and addresses the challenge of modern malware.
How does it work? Unknown and potentially-malicious files are executed in a cloud-based sandbox. If the files are confirmed to be malicious, it automatically generates new signatures for both the file and for any traffic generated by the malicious file. These signatures are distributed with regular signature updates. Plus, you get an actionable analysis of exactly how the malware behaves – who was targeted and what application delivered the threat.
That sounds great, but how do I use it? At this time, WildFire is a free feature included with PAN-OS 4.1 or newer. If you already own a Palo Alto Networks firewall, enable it!
- Login to your firewall and go to Device > Setup > WildFire
- Go with the defaults settings, or make changes based on your requirements.
- Configure file blocking profiles (PE file type) to include the “forward” or “continue-and-forward” action.
- Incorporate file blocking profiles in security policies, just like other file blocking profiles.
That’s all you need to do on the firewall. Now login to the WildFire portal:
- Go to https://wildfire.paloaltonetworks.com, and login with your support credentials.
- Optional: Change your time zone and/or email notification settings.
- The initial screen is the dashboard, similar to the following:
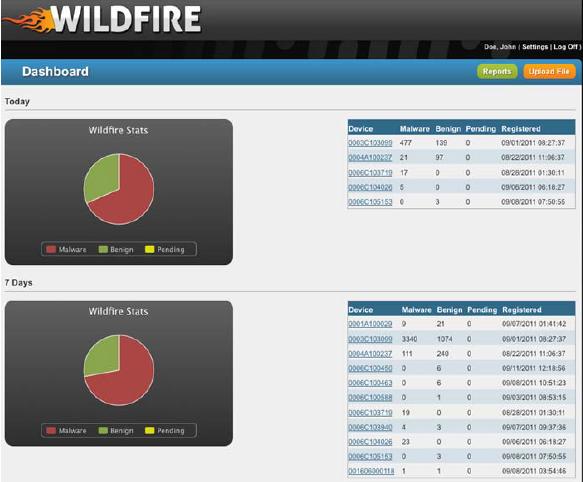
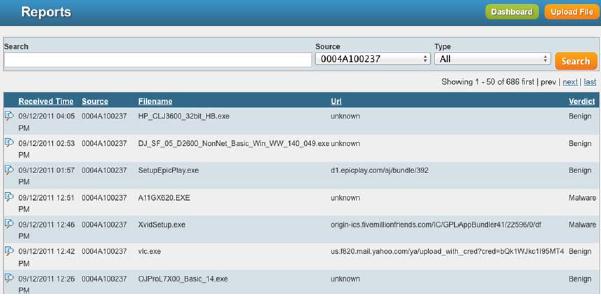
- Click the ‘Reports’ button to see details of the potential and actual threats that have been processed in the cloud:
Do you have any interesting stories about WildFire, or thoughts about this article? Please chime in with a comment.





