
Vulnerability management can absolutely be the lifeline of protecting your organization or being at risk for something bad to happen, cough cough...Equifax. One of the most “simple” security protocols is to patch your machines. For some reason, time after time, we see a failure to do so. Though vulnerability management is not all about patching, patching plays a major role in the security posture of any organization.
Why do we constantly see breaches due to unpatched systems? Patching is mundane? IT teams are spread thin and spend their time fighting fires or working on projects? We have all been there.
So, let’s work backwards, when vulnerability management is done poorly, we get the ugly. We get Equifax. The Verizon Data Breach Report for 2016 stated that most vulnerabilities dated back to 2007, aka there has been an absolute neglect to patch systems for almost 10 years. If you ask me there is a man power issue here.
Now let’s look at the bad, the bad is every other company that has been breached due to poor vulnerability management. These companies were just fortunate enough to stay out of the limelight and/or maybe not have as detrimental consequences.
So, what is the good? The good is a security team that is absolutely on top of their patching and vulnerability management. It is looking at servers, devices, end-point and having a prioritized list of the most at risks applications. Then having the steps in place to fill those security gaps that will tighten security immediately. It is a team that is running automation to discover these vulnerabilities and applying their resources on an as needed basis to mitigate the risks at hand. It is simple and effective. But if so simple and effective, why aren’t we all there?
If you ask me, it comes down to the three things that effect IT across the board: time, budget, and resources. Typically, in vulnerability management, I think it really comes down to time and resources.
Whether it is time or resources, there is one tool and service that plays a key role in the security puzzle and can give back time and resources to focus on projects and proactive security initiatives.
Rapid7’s vulnerability management tool known as Nexpose and InsightVM not only has beautiful, user-friendly dashboards, they make automated discovery of vulnerabilities and mitigation across your entire environment extremely efficient and easy. When automated discovery is enabled, quantifiable data is produced, and vulnerabilities become prioritized as the riskiest (needing attention immediately) to the least risky. This takes out the leg work of reviewing massive data sets and trying to understand which vulnerabilities matter and which ones can be ignored.
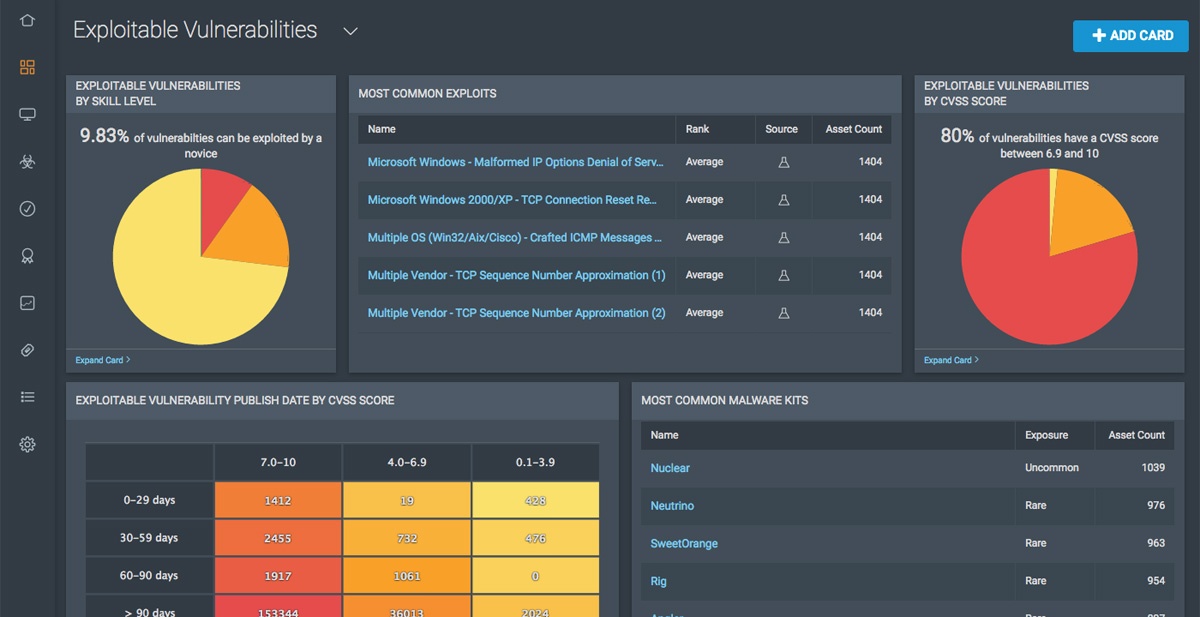
Then there is mitigation. Sometimes your team may be able to take care of remediation once vulnerabilities are discovered but maybe there is not enough resources to consistently remediate these things. That is where vulnerability management as a service comes into play. This service wraps it all together from automated continual discovery, prioritization of vulnerabilities discovered, and remediation of the most at risk vulnerabilities. This not only gives you the data to understand where you have vulnerabilities but also gives you the information of when vulnerabilities have been resolved and how much risk has been managed. YOu can then generate a simple report that can then be handed over to management to have visible, quantifiable data and proof that you are managing risk successfully.
This is “The Good” when talking about vulnerability management.
If you would like to learn more and/or see a Rapid7 demo please feel free to email, call, or text me at mhannula@birdrockusa.com or (805) 305-8773.




